Methods You Can Easily Implement To Make your VPN more secure
VPNs seem like the most secure things in the world. In a world that is going through increasing levels of online risks, using a VPN ensures your privacy and security online remains safe and as high as possible.
However, what if you wake up one day, only to find that your VPN service of choice is going through an unfortunate incident? Such as hacking?
What would you do?
A VPN service, as its default, is meant to give you excellent levels of privacy and security, but they are made by humans, for humans – and that makes them easy to crack at certain unfortunate times. Therefore, if you want to be more secure, there are ways you can increase your protection factor – even while using the most secure VPN.
Table of Contents
Ways to up your security

Change the protocols you use
The basic of VPNs is always the protocol, which is how the network encrypts incoming and outgoing traffic. That said, there is not just one kind of VPN – there are actually several protocols that are in common use, and the good news is that numerous providers will provide you with a choice that works for you.
In some cases, you will find that the choice is available in the app, while in others it will be an option you can use to configure a third-party VPN tool.
You will notice that the most common protocols are the OpenVPN (an open-source VPN protocol), L2TP/IPsec (protocol for layer 2 tunneling, very secure) and PPTP (an older protocol that is still quite common, though not as safe).
If you happen to be using a flashed VPN router or a mobile device, using L2TP or PPTP is a good choice, since they are easier to configure. You will also require a username, server name, and password.
However, regardless of the device you use, the OpenVPN option is the best. The reason that makes PPTP unsafe at times is due to its 128-bit encryption. Moreover, the process of authentication and initial connection can sometimes be intercepted by other people, and the information compromised. On the good side though, it is among the fastest protocols as it has the lowest encryption process.
L2TP is usually among the most secure, though the double encryption process makes it quite slow. On the other hand, OpenVPN is a great balance between the two: it has high levels of security, and recovers very quickly from lost connections.
Using the kill switch

There comes a major problem with using VPNs – sometimes the connection will fail. When this happens, the device immediately goes back to the regular internet address you use, which makes you vulnerable (this is referred to as an IP leak). The greater danger here though – you will likely have no idea it even happened.
This is where the kill switch is your best friend. It will make sure that when you suddenly lose the VPN from your connection, it will immediately shut it down, or all the apps that use it.
Certain VPN connection apps will have a kill switch integrated in their design, and it is better for you to enable it.
If the app does not have the feature, then the alternative is a software kill switch, which you can add to all VPNs. They include apps such as VPNetMon, which you configure on the Windows platform to close the selected apps when the VPN dies.
Enable network locks
This is an easy way to ensure secure connections, and works in the same way as a kill switch. When the Wi-Fi and VPN get interruptions, the network lock prevents the device from accessing the internet, until the VPN reconfigures itself. However, you should note that not all VPN service providers have the feature.
Stopping DNS leaking
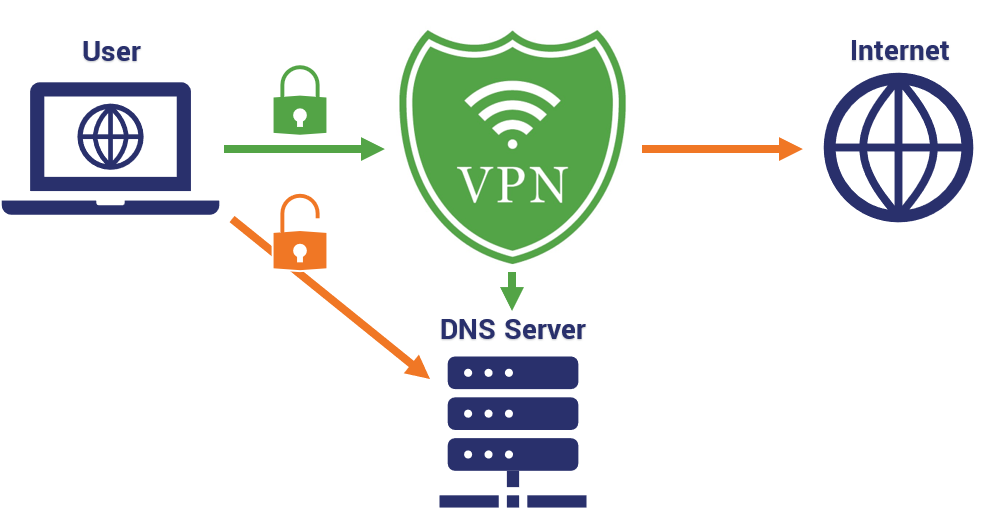
What is DNS, you may ask?
Well, a DNS, which also means a Domain Net Server, is the service the computer will use to convert a URL into an IP address.
When you connect your network to a VPN, you should be instantly using the VPN service’s secure DNS server. However, sometimes this is not the case, as the device might be using its usual DNS connection when it bypasses the VPN. The result is known as a DNS leak, and any outside forces that are interested in your data can see your activities on the internet.
Certain VPN apps and clients have in-built DNS protection, but you can always check if you are unsure. When conducting the test, the resulting location it should tell you is that you are in the ‘apparent’ VPN location (where the server you chose is), instead of your actual location.
Blocking any leaks of IPv6
Regarding most activities on the internet, we usually rely on version 4 of the internet protocol system =- that means, the one that uses the 4-number IP address. What you may not know is that a version 6 exists, and this will give you many more addresses than the IPv4. A typical computer will support both, though internet providers are still transitioning to the v6.
The thing about the version 6 though – it operates outside of VPN limits; which means that any attacker can use it to figure out who you are. Even though it does not happen frequently, it still does, so the only way to prevent it is disabling the v6. Some VPNs have this ability built-in, but you can also accomplish it manually.
Preventing WebRTC leaks

It is also essential to prevent your network from exposing your IP address unwittingly. The Web Real-Time Communication (WebRTC) is the protocol that enables two devices to broadcast each other’s IP addresses and communicate to each other.
Unfortunately, this will expose your location at times – even when you use a VPN.
The best way to prevent this is using IP testers to note your address both before and after connecting to a VPN – if it is blocking the WebRTC, the IP address should change after connecting to the VPN. You can also use ad blockers as well.
Final thoughts
VPNs will work as a useful layer of added security on top of an antivirus program, and they are always the next step when you want to be conscious about how you use the internet. However, it is important to continue taking measures to keep yourself safe when using them, since they can also experience issues at times.
Also Read: Top Most Common Types Of Cyberattacks